Port Security Overview
You can use the port security feature to limit input to associate interface by limiting and distinguishing mac
addresses of the workstations that are allowed to access the port. once you assign secure mac addresses to a
secure port, the port doesn’t forward packets with source addresses outside the cluster of outlined addresses. If
you limit the amount of secure mac addresses to 1 and assign one secure mac address, the digital computer
connected to it port is assured the total bandwidth of the port.
If a port is designed as a secure port and therefore the most range of secure mac addresses is reached, once the
mac address of a digital computer trying to access the port is totally different from any of the known secure mac
addresses, a security violation happens.
After you have got set the maximum range of secure mac addresses on a port, the secure addresses are
enclosed in an address table in one among these ways:
You will set up all secure mac addresses by exploitation the switchport port-security mac-address
mac_address interface configuration command.
You will enable the port to dynamically set up secure mac addresses with the mac addresses of connected
devices.
You will set up variety of addresses and permit the remainder to be dynamically configured.
You can configure mac addresses to be sticky. These may be dynamically learned or manually configured,
keep within the address table, and additional to the running configuration. If these addresses are saved
within the configuration file, the interface doesn’t ought to dynamically learn them once the switch restarts.
though sticky secure addresses may be manually configured, it’s not suggested.
You can configure an interface to convert the dynamic mac addresses to sticky secure mac addresses and to
feature them to the running configuration by enabling sticky learning. To change sticky learning, enter the
switchport port-security mac-address sticky command. once you enter this command, the interface converts all
the dynamic secure mac addresses, together with those who were dynamically learned before sticky learning was
enabled, to sticky secure waterproof addresses.
The sticky secure mac addresses don’t mechanically become a part of the configuration file, that is that the
startup configuration used anytime the switch restarts. If you save the sticky secure mac addresses within the
configuration file, once the switch restarts, the interface doesn’t ought to learn these addresses. If you are doing
not save the configuration, they’re lost.
If sticky learning is disabled, the sticky secure mac addresses are born-again to dynamic secure addresses and
are removed from the running configuration.
After the most variety of secure mac addresses is configured, they’re keep in an address table. to confirm that an
connected device has the complete information measure of the port, configure the mac address of the connected
device and set the most variety of addresses to 1, that is that the default.
Port Security Violation
A security violation happens if the most variety of secure mac addresses has been additional to the address table
and a digital computer whose mac address isn’t within the address table tries to access the interface.
You can tack together the interface for one among these violation modes, supported the action to be taken if a
violation occurs:
Restrict—A port security violation restricts knowledge, causes the Security Violation counter to increment,
and causes an SNMP Notification to be generated. the speed at that SNMP traps are generated may be
controlled by the snmp-server modify traps port-security trap-rate command. The default price (“0”) causes
an SNMP trap to be generated for each security violation.
Shutdown—A port security violation causes the interface to shut down immediately. once a secure port is
within the error-disabled state, you {can|you’ll|you’ll be able to} bring it out of this state by coming into the
error disable recovery cause port secure-violation global configuration command otherwise you can
manually re enable it by coming into the shutdown and no shut down interface configuration commands.
this can be the default mode.
You can conjointly customize the time to get over the desired error disable cause (default is three hundred
seconds) by coming into the error disable recovery interval interval command.
Port Security Topology
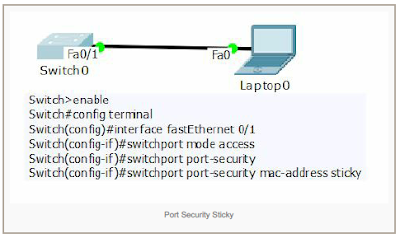
Port Security Sticky Configuration
Switch>enable
Switch#config terminal
Switch(config)#interface fastEthernet 0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport port-security
Switch(config-if)#switchport port-security mac-address sticky


EmoticonEmoticon